 Anti-intrusion systems are gaining popularity today, but it’s essential to clearly understand the desired outcomes to implement the most suitable measures for protection objectives.
Anti-intrusion systems are gaining popularity today, but it’s essential to clearly understand the desired outcomes to implement the most suitable measures for protection objectives.
Our solutions are specifically designed to meet our clients’ needs in terms of intrusion detection technology.
VIGILANCE: The goal is to detect unwanted presence, sound the alarm immediately, and intervene as quickly as possible. Simultaneously, resist using all mechanical and electronic means to slow the intruder’s progress or prevent access to sensitive areas.
TECHNOLOGY: The variety of wired or wireless equipment allows the detection system to be tailored to security objectives and specific usage and operational needs.
ABSOLUTE WEAPONS AGAINST INTRUDERS:
- In case of intrusion, activation of deterrence systems and sending alerts (SMS, email, etc.).
- Remote monitoring.
OPERATION: The objectives that align with operational requirements are:
- Management of multiple independent sectors (PARTITION).
- Specific functions: chime, time delay, automation.
- Scheduling of activation and scenarios.

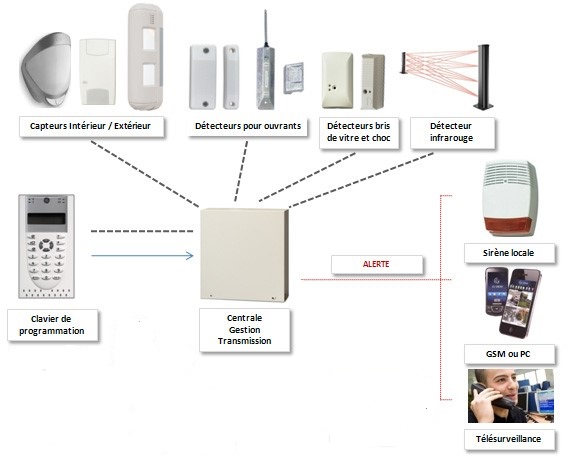
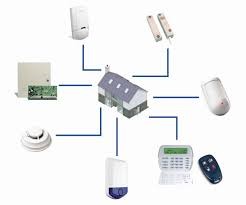
 It centralizes all information from detectors and alerts when necessary. It connects sensors, the siren, and alert transmission. Controlled by a remote or keypad, it also manages the entire alarm system’s operation (activation, deactivation, etc.). A transmitter for communication (RTC, GSM, IP, or GPRS) is often integrated into the control unit in newer models.
It centralizes all information from detectors and alerts when necessary. It connects sensors, the siren, and alert transmission. Controlled by a remote or keypad, it also manages the entire alarm system’s operation (activation, deactivation, etc.). A transmitter for communication (RTC, GSM, IP, or GPRS) is often integrated into the control unit in newer models.

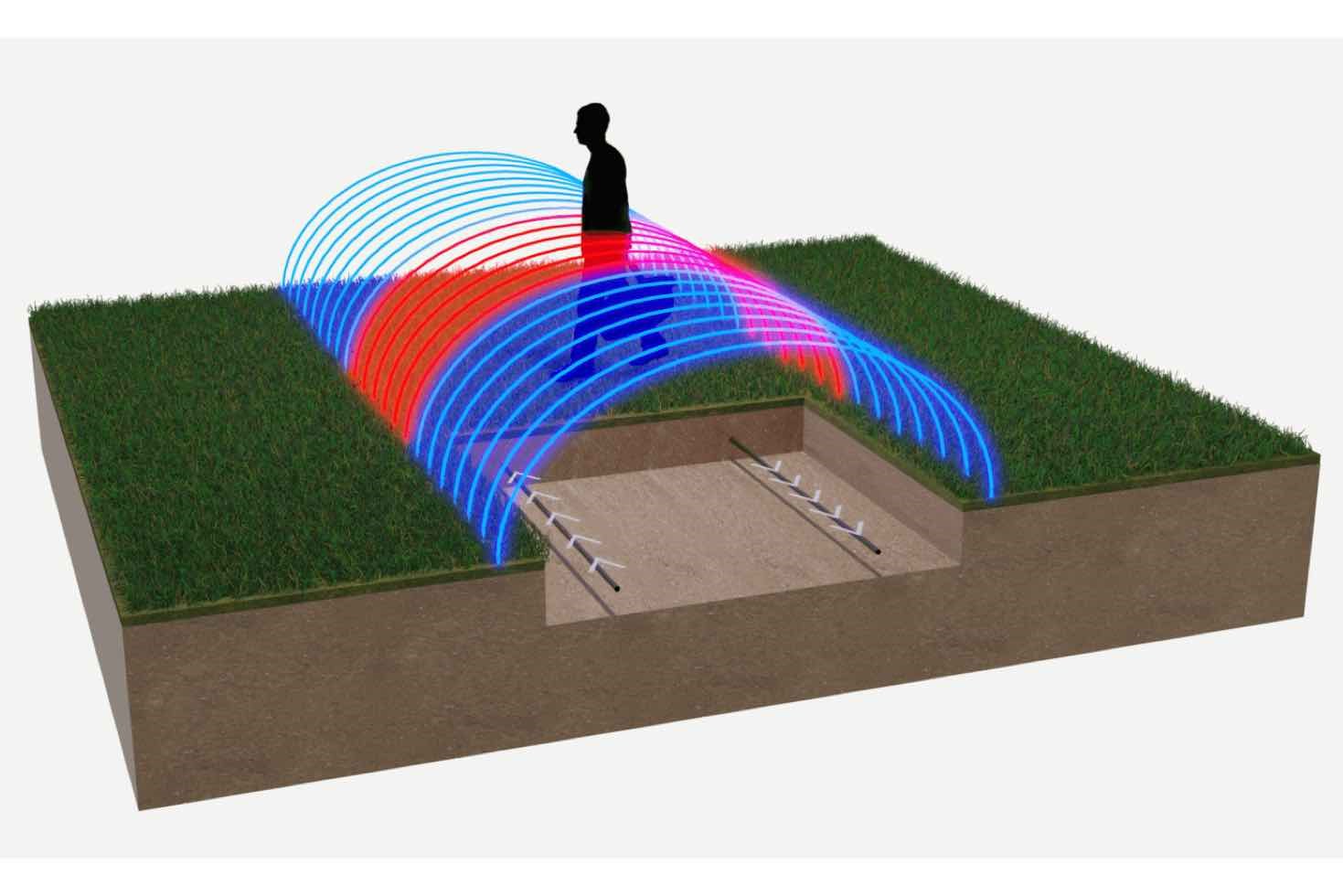
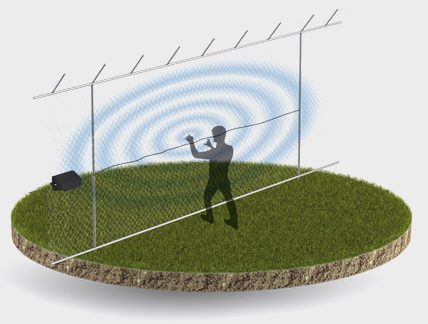
The most common technology combines IR (infrared) and microwave detection. Volumetric detectors can be installed indoors or outdoors and monitor a specific volume or area based on angle and height. They use infrared sensors and thermal energy. For remote verification, some detectors include a micro-camera and flash. Most detectors are configured to avoid false alarms triggered by pets.